Chinese SMS Phishing Group Targets iPhone Users in India Following Scam
A sophisticated SMS phishing campaign by the Chinese Smishing Triad targets iPhone users in India, exploiting India Post and iMessage to deceive victims. Learn about the tactics used, the implications of this scam, and how to protect yourself from such phishing attacks.

The infamous Chinese Smishing Triad gang, known for its extensive SMS phishing attacks against Pakistan, the US, and several European countries, has now shifted its focus to iPhone users in India. This group is exploiting both iMessage and the government-operated India Post in a new, sophisticated phishing scam.
FortiGuard Labs has uncovered an advanced Smishing (SMS phishing) campaign targeting users of India Post, India’s government postal service. The scam, attributed to the China-based Smishing Triad, involves sending deceptive iMessages to iPhone users, falsely claiming that a package is awaiting pickup at an India Post warehouse.
The fraudulent messages often contain a short URL that directs recipients to a counterfeit website designed to closely resemble the official India Post site. Victims are then prompted to enter sensitive personal information, including their name, residential address, email ID, and phone number. In some cases, the scammers also request credit card details under the pretense of a minor redelivery fee.
FortiGuard Labs' investigation revealed that from January to July 2024, over 510 domain names were registered to impersonate India Post’s official domain. Notably, 297 of these domains were registered through a Chinese registrar, Beijing Lanhai Jiye Technology Co., Ltd., raising significant concerns about the campaign’s origins and intentions.
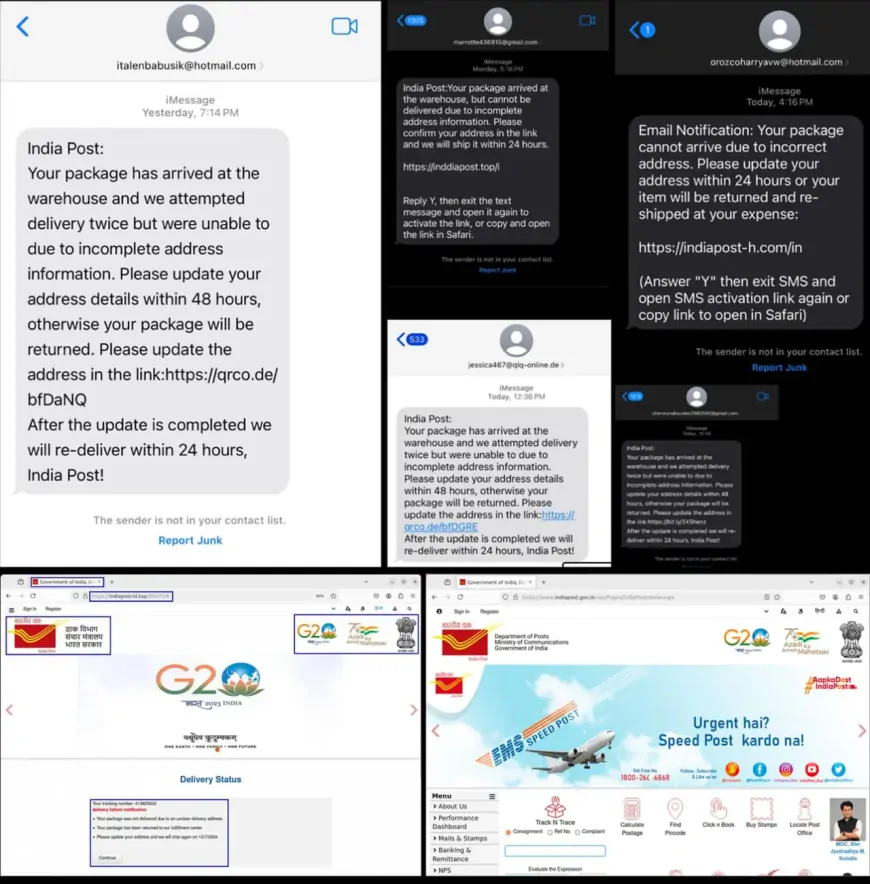
Malicious text messages received by users – One of the fake India Post domains used in the scam (Credit: FortiGuard Labs)
The Smishing Triad has previously targeted various regions, including the US, UK, EU, UAE, KSA, and Pakistan. Their approach involves using third-party email addresses—such as Hotmail, Gmail, or Yahoo—to create Apple IDs and send phishing messages via iMessage. This method enables the scammers to circumvent traditional email security measures and reach users directly on their iPhones.
According to a report from Fortinet Labs, shared with Hackers4u.com before its official release on Thursday, the phishing campaign is highly sophisticated and meticulously organized. The expenditure on registering malicious domain names alone surpasses USD 1500.
Jason Soroko, Senior Vice President of Product at Sectigo, stressed the gravity of the situation: “The exploitation of third-party email addresses via iMessage facilitates these attacks, highlighting the urgent need for increased awareness and robust security measures to prevent potential financial losses and data breaches.”
Stephen Kowski, Field CTO at SlashNext Email Security+, underscored the critical need for comprehensive mobile web threat protection: “As smishing attacks become more advanced, it’s essential for organizations to educate users on how to identify and report suspicious messages. Implementing strong security measures that can detect and mitigate threats in real-time, across all communication channels, is vital.”
To protect against such scams, users should be cautious with unexpected emails or messages, verify URLs before clicking, and refrain from sharing personal information via email or messaging apps. Enabling multi-factor authentication and keeping software updated are also important steps to enhance account security.
What's Your Reaction?





























































